In Linux/Unix like operating systems everything is logged. Many valuable log files are automatically created for you by Linux. You can find them in your /var/log directory.
This folder contains logs related to different services and applications. In this folder apart from other logs files we have some files such as utmp, wtmp and btmp. These files contains all the details about login’s and logout’s which are from local as well as from remote systems and system status such as uptime etc.
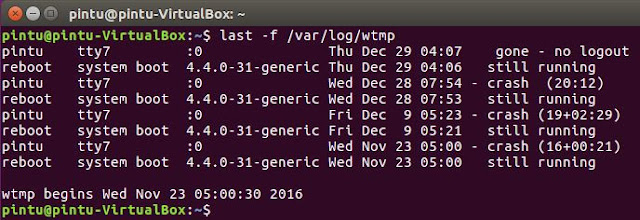
Some info about utmp, wtmp and btmputmp will give you complete picture of users logins, logouts, system events, Which terminal was used and current status of the system, system boot time (used by uptime) etc.
wtmp gives historical data of utmp.
btmp records only failed login attempts.
Normally when we try to view these files using "cat" command or "vi" editor they will show some junk characters and garbage values or in encrypted form or hex values as these files are not regular text files, but rather a binary format which needs to be edited by some special programs The output of these files when open with vi or cat command are shown below to show how wtmp file look when opened with vi.
btmp records only failed login attempts.
Normally when we try to view these files using "cat" command or "vi" editor they will show some junk characters and garbage values or in encrypted form or hex values as these files are not regular text files, but rather a binary format which needs to be edited by some special programs The output of these files when open with vi or cat command are shown below to show how wtmp file look when opened with vi.
The implementation and the fields present in the file differ depending of the system or the libc version, and are defined in the utmp.h header file. The wtmp and btmp format are exactly like utmp except that a null value for "username" indicates a logout on the associated terminal (the actual user name is located by finding the preceding login on that terminal).
Furthermore, the value "~" as a terminal name with username "shutdown" or "reboot" indicates a system shutdown or reboot (respectively).
Furthermore, the value "~" as a terminal name with username "shutdown" or "reboot" indicates a system shutdown or reboot (respectively).
Then how we can read this file?
On the Linux systems there are three standard commands that show the information about last logged in users: last, lastb and lastlog
The output of these commands include: login name, last login time, IP address, port etc.
lastlog is a program available on most Linux distributions. It formats and prints the contents of the last login log file, /var/log/lastlog, including the login name, port, and last login date and time. It is similar in functionality to the program last; however, last parses a different database (wtmp and btmp).
Command
|
Logfile
|
Description
|
Last
|
/var/log/wtmp
/var/run/utmp
|
Lists successful login/logout history
|
Lastb
|
/var/log/btmp
|
Shows the bad login attempts
|
Lastlog
|
/var/log/lastlog
|
Shows the most recent login
|
Watch the catch here : **Never logged in**
Whereas the earlier command showed that pintu had logged in, this is by design, lastlog file records remote logins only, it doesn't log local login.
To remove all the information about the last logged in users, you have to clear the files where the information is kept
Echo > /var/log/wtmp
Echo > /var/log/btmp
Echo > /var/log/lastlog
Echo > /var/log/wtmp
Echo > /var/log/btmp
Echo > /var/log/lastlog
Echo > /var/run/utmp



Comments
Post a Comment